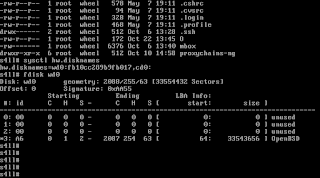
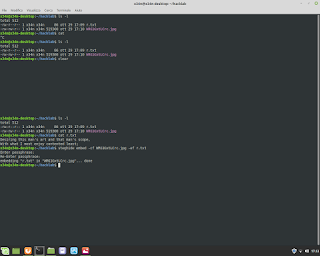
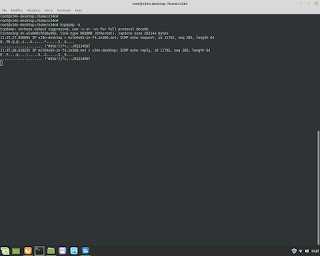
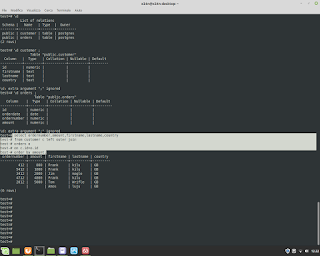
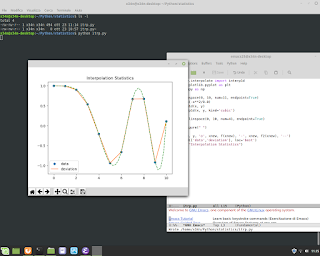
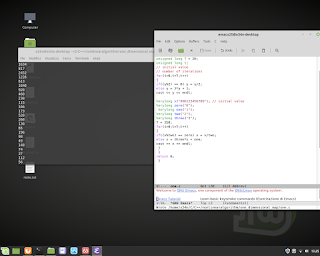
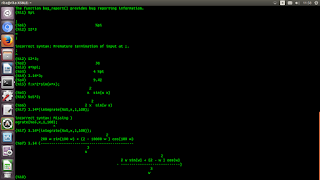
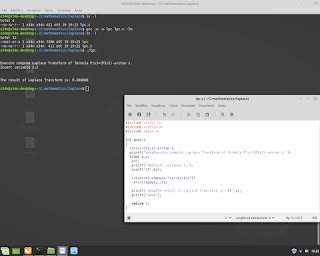
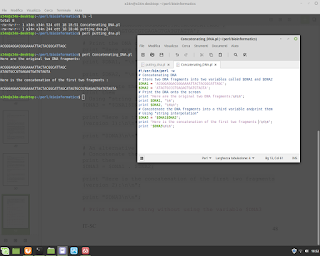
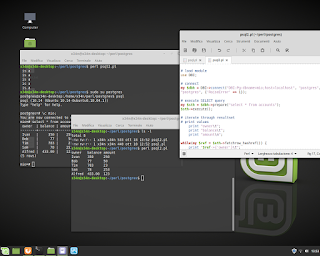
C Language and Mathematics. In this example execute a regression for equation y=a+bx.
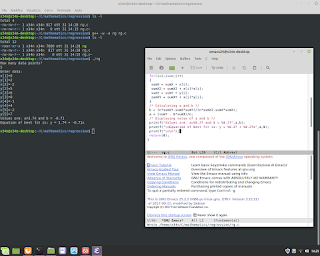
C Language and Mathematics. In this example execute a regression for equation y=a+bx. Below an example. #mathematics #c #gcc #programming #unix #linux #bsd #backend #research #fullstack #businessintelligence #physics #shell #bash