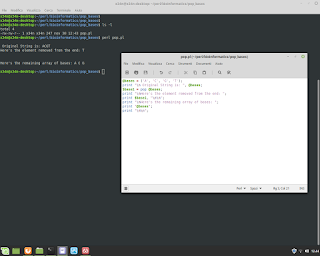
C Language and how to manage list with node. In this example use struct for manage nodes.
C Language and how to manage list with node. In this example use struct for manage nodes. #nodes #list #fifo #lifo #c #gcc #unix #linux #backend #fullstack #programming #research #mathematics #physics