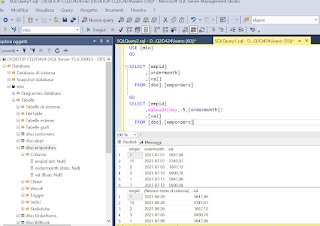
C Language on Linux and Postgresql Database. Below, and example which how to perform a connection with code C.
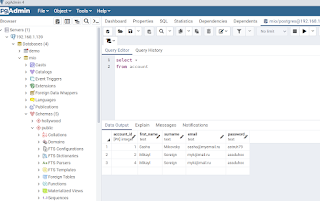
C Language on Linux and Postgresql Database. Below, and example which how to perform a connection with code C. #c #gcc #dba #database #postgresql #pgsql #sql #query #aws #onpremise #linux #programming #cloud