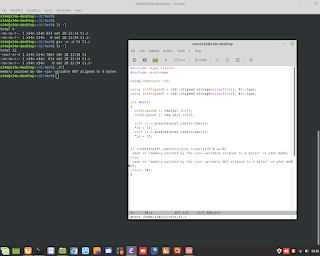
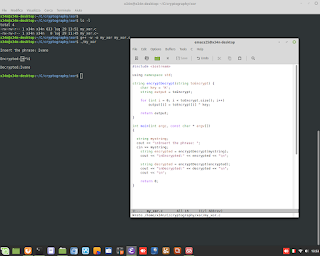
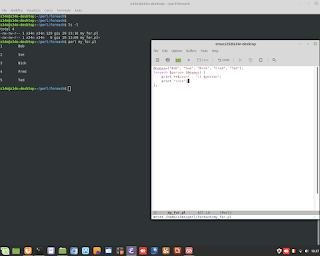
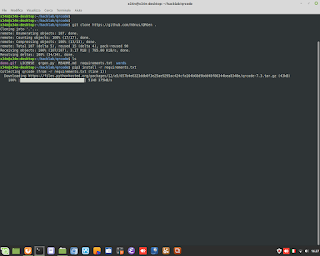
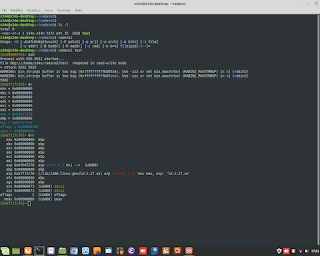
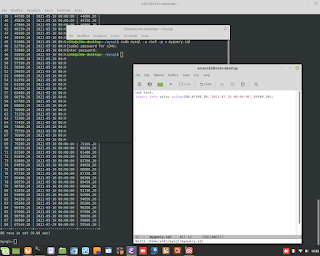
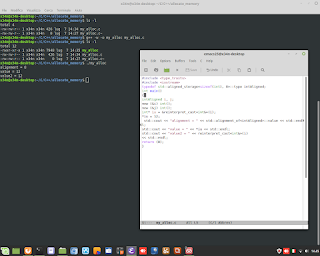
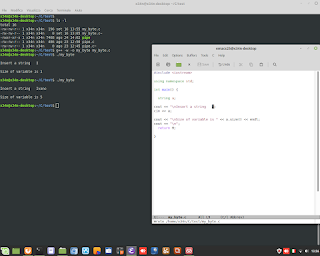
Perl is Language very clever. In thi example, show how to sum number to alphanumeric string. Perl is able to understand to add only numbers.
Perl is Language very clever. In thi example, show how to sum number to alphanumeric string. Perl is able to understand to add only numbers. #perl #programming #clever #backend #research #developing #genoma #dna #bioinformatics #hacking