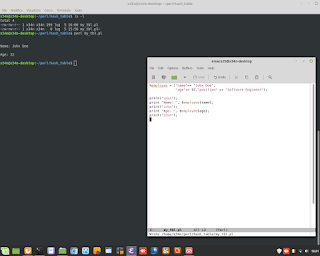
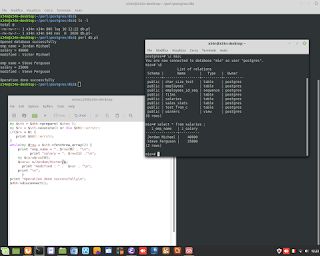
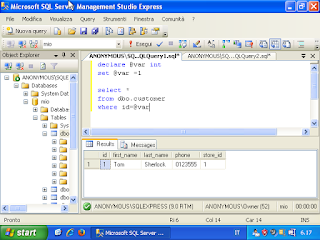
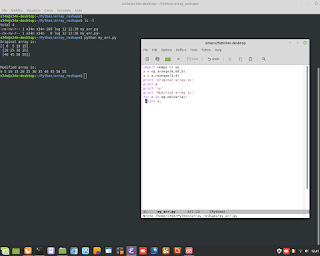
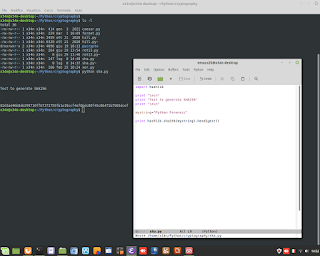
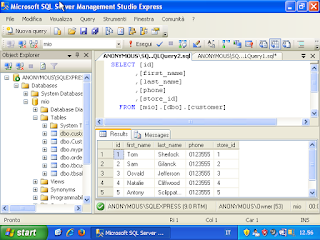
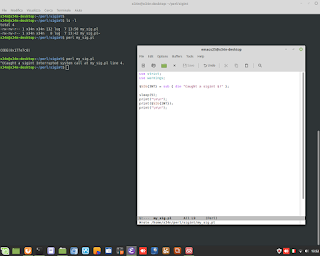
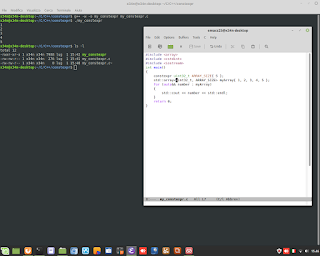
Perl Language and TCP Client/Server application.
Perl Language and TCP Client/Server application. #perl #netcat #nc #tcp #client #server #backend #CyberSecurity #ethicalhacking #programming #developer #linux #unix
Senior Database Administrator,PostgreSQL, MsSqlServer, Mysql,Sybase,Oracle.Ethical hacker,Linux/Unix Administrator.C/C++,Perl,Python,Bash,PHP,Migration Expert.