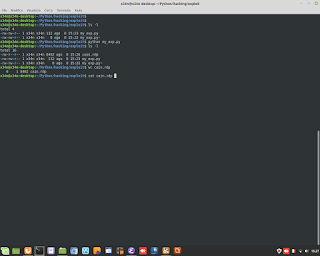
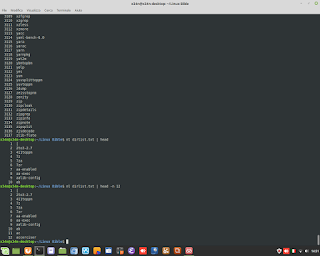
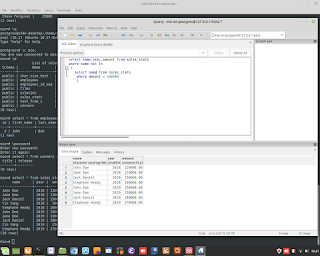
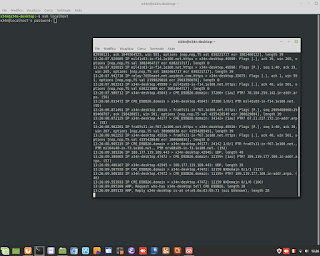
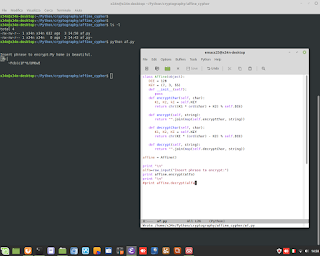
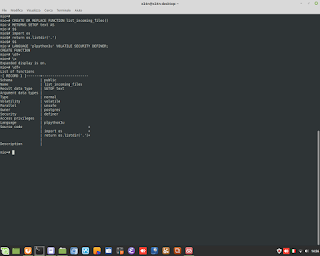
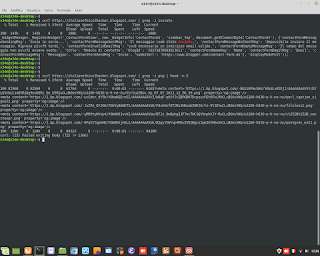
Euclid's Theorem in C Language for Encryption.
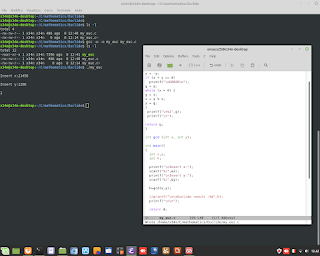
Euclid's Theorem in C Language for Encryption. #mathematics #c #gcc #programming #backend #euclid #encryption #cryptography
Senior Database Administrator,PostgreSQL, MsSqlServer, Mysql,Sybase,Oracle.Ethical hacker,Linux/Unix Administrator.C/C++,Perl,Python,Bash,PHP,Migration Expert.