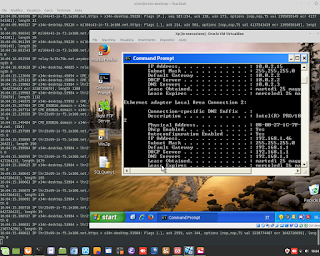
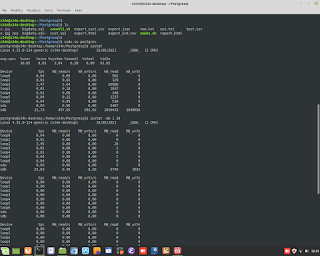
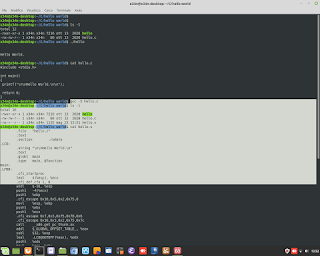
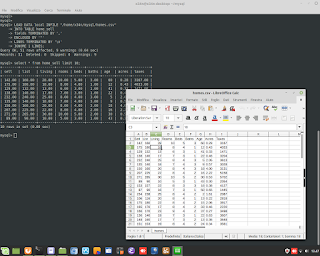
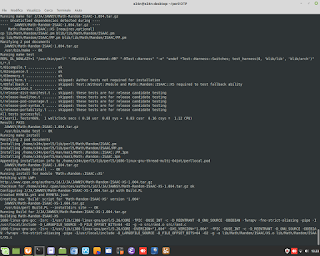
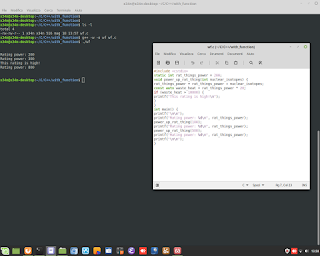
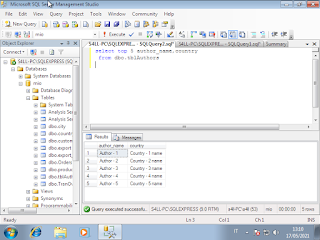
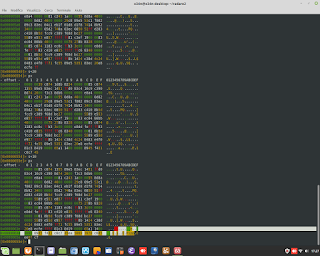
Cyber Security / Ethical Hacking. A simulation of attack DDOS, and gathering information about it, through the sniffer/tool 'tcpdump'.
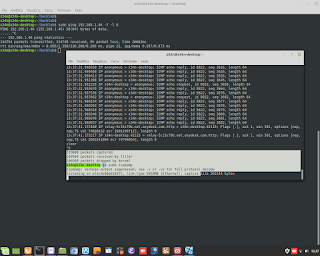
Cyber Security / Ethical Hacking. A simulation of attack DDOS, and gathering information about it, through the sniffer/tool 'tcpdump'. #ddos #attack #hacking #ethicalhacking #cybersecurity #malware #ramsomware #penetrationtesting