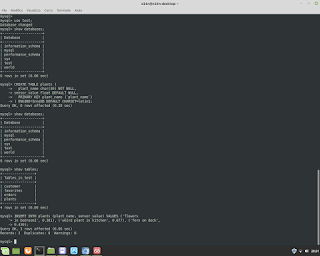
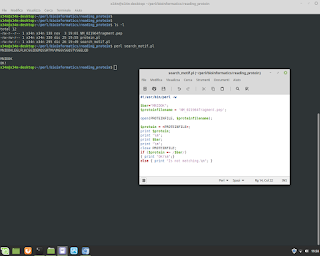
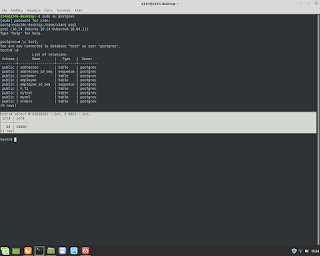
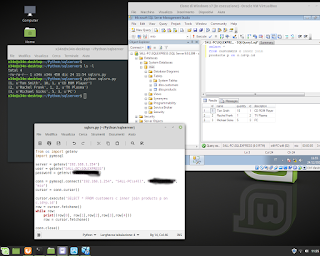
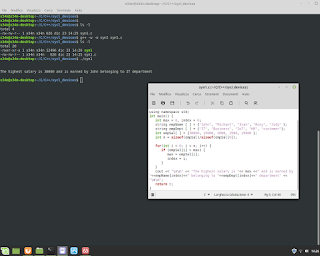
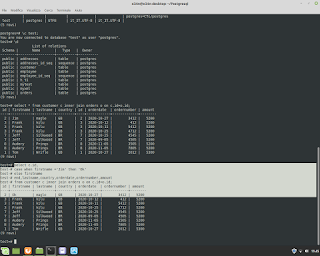
Postgresql Database Administration. How to use a 'foreign key' in the table.
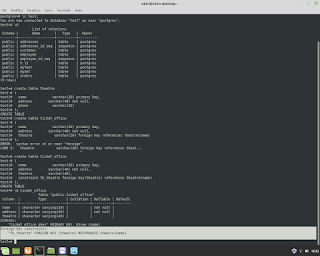
Postgresql Database Administration. How to use a 'foreign key' in the table. Example. #postgresql #dba #database #sql #foreignkey #backend #fullstack #reporting #normalization #integration