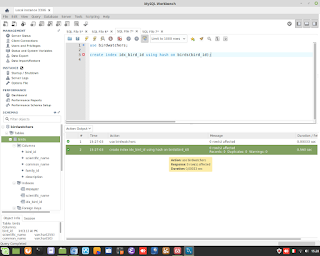
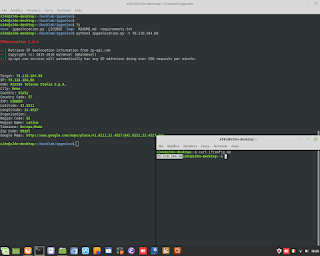
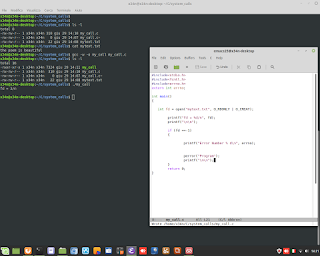
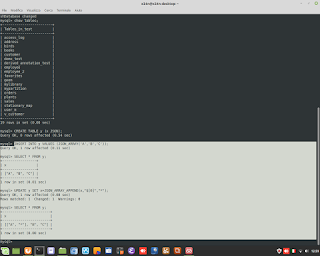
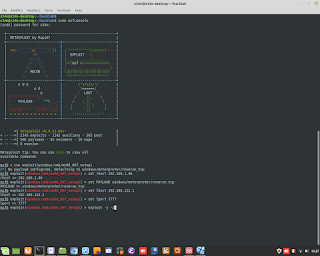
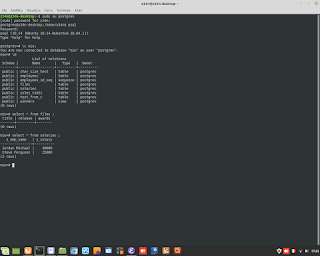
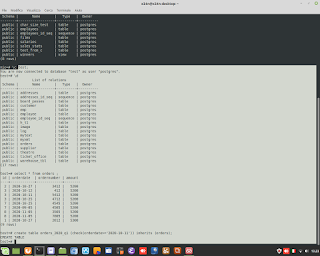
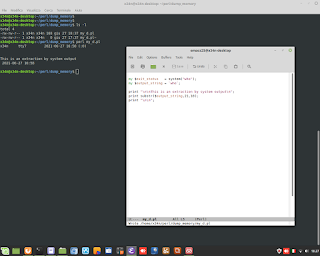
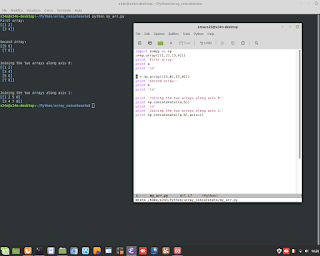
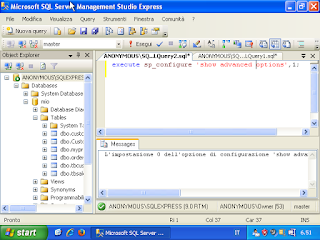
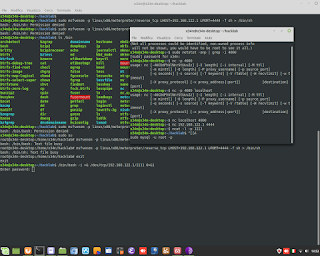
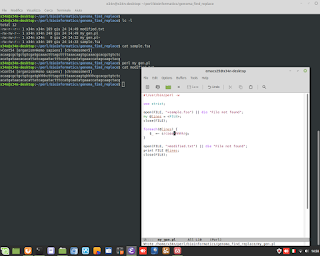
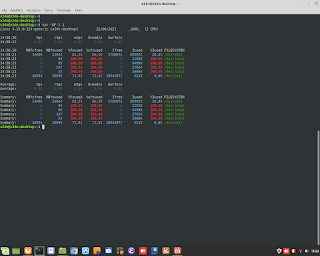
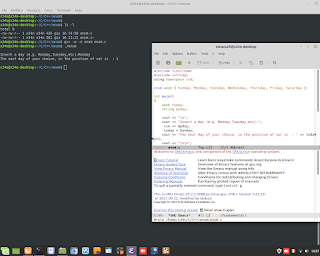
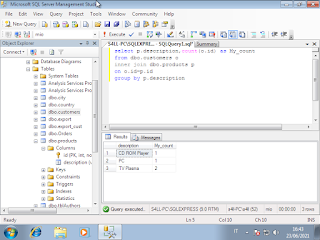
Windows Admin/Powershell How to. Below, two example for monitoring Systems.
Windows Admin/Powershell How to. Below, two example for monitoring Systems. #powershell #windows #administrator #script #systems #engineering #aws #cloud
Senior Database Administrator,PostgreSQL, MsSqlServer, Mysql,Sybase,Oracle.Ethical hacker,Linux/Unix Administrator.C/C++,Perl,Python,Bash,PHP,Migration Expert.