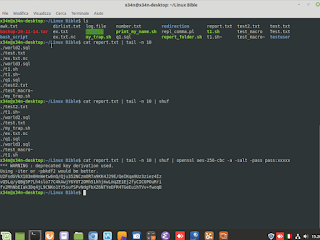
Linux Encryption. How to create private key with openssl tool, and extract a relative public key, for sharing.
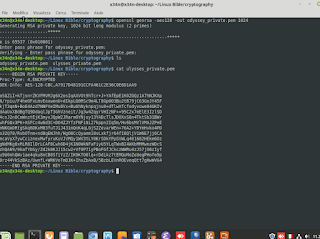
Linux Encryption. How to create private key with openssl tool, and extract a relative public key, for sharing. #linux #administration #openssl #cybersecurity #encryption #cryptography #privatekey #publickey