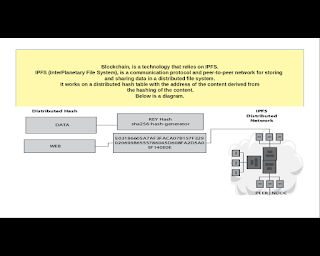
Blockchain is a robust and interesting technology, but is not free from cyber attack, especially for code errors. Below an example.

Blockchain is a robust and interesting technology, but is not free from cyber attack, especially for code errors. Below an example. #blockchain #programming #hacking #cybersecurity #ethicalhacking #malware #osint #backend #aws #cloud #bitcoin