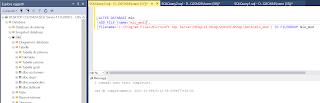
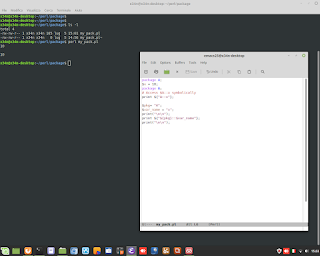
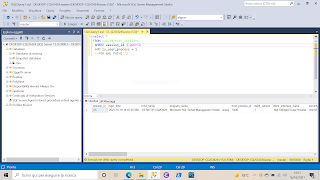
Ethical Hacking and Scanning with tool 'nmap', in modality 'stealth'.
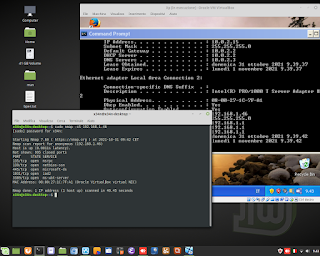
Ethical Hacking and Scanning with tool 'nmap', in modality 'stealth'. An example. #cybersecurity #ethicalhacking #hacking #nmap #penetrationtesting #malware #virus #Ransomware